Late last year, in a span of under two weeks, I received dozens of political spam texts around Austin’s Prop A ballot measure. I’m sure countless people around the world also get unsolicited garbage texts.
Such text campaigns threaten to alter voter turnout and turn people against each other. Because SMS texts lack authentication, users can’t know who actually sent them, nor can we effectively block them. As the screenshot below demonstrates, “Sam” from “SaveAustinNow” texted me from several different numbers:
Here’s a collage of some of the texts I received during this period. Many are written to scare the recipient and most contain falsehoods. Notably these texts don’t even pretend to include opt-out language (not that they would honor such language anyway).
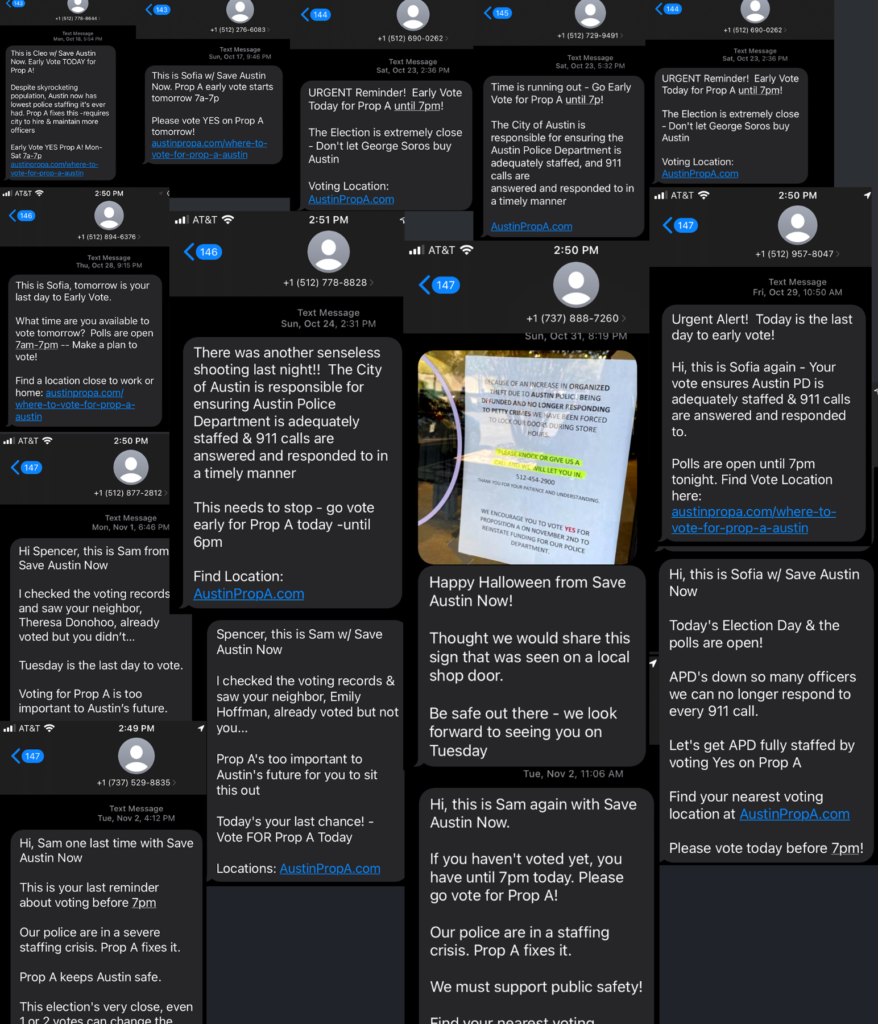
The worst ones are those that claim a neighbor of mine “already voted but not you…”, these kind of stalker-y texts must work because official GOP accounts are using them all over the place, lately to promote/push Trump’s “Truth Social” platform. (I also received texts from the other side of the Prop A issue, but those included options to “stop” texts from continuing.)
Everyone carrying a phone, even a $1500 iPhone Pro Max or $2K Samsung Fold, can receive unsolicited texts from anywhere in the world. Womp womp. Anyone in the world can use a Twilio-like SMS service to send unsolicited texts. This leaves citizens of any country open to getting disinformation pushed to them from foreign actors hoping to influence at scale. Sounds crazy? Well, just a few days ago a massive campaign to pepper Russian numbers with unsolicited texts found success — it cuts both ways. That SaveAustin campaign that hit me? There is no way for me to know who was behind it – it could just as easily be foreign actors as genuine SaveAustin people – the texts lack authentication.
Getting unsolicited texts is not just annoying, it’s a security hazard – thanks to an attack vector called “zero click“, where texts themselves can carry a malicious package capable of hacking your phone, regardless of whether you click on them or not. At various points in recent years, modern up-to-date smartphones have been actively exploited by such attacks.
What can be done? Well, one step that carriers have talked about is adopting an authentication protocol called STIR/SHAKEN, so that customers can know when a text/call coming from a number is legitimate. But it’s been years and, despite federal requirements for carriers to roll out the tech by mid-last year, everyone can see from the screenshots in this article that spam text campaigns continue unabated. Furthermore, Apple has never made it clear to this AT&T customer (in iOS) if a call or text was “authenticated”. It’s almost as if they would like our experience with SMS to be complete garbage so that we are more locked in to iMessages (a sentiment that has led iMessage product decisions before). In other words, there has been very little progress on this front for end users.
If you enjoyed this post, my last one may interest you as well – as it explores the emerging threat of robocalls backed with deepfake audio and similarly makes the case for expedited STIR/SHAKEN adoption.